
Photo by Towfiqu barbhuiya on Unsplash
What can go wrong in a cryptographic system?
An enumeration and brief description of parameters that should be considered while designing and developing a secure cryptographic system.
What can go wrong in a cryptographic system?
Recall, cryptography is the study of techniques to securely exchange information between sender and an intended recipient. Encryption is the act of converting plain text into cipher text based on the input key and one or more parameters that make the cipher text non-deterministic. While, decryption is the act of converting a given cipher text back to plain text based on the key that was used for encryption to evaluate the cipher text.
How cryptographic systems work?
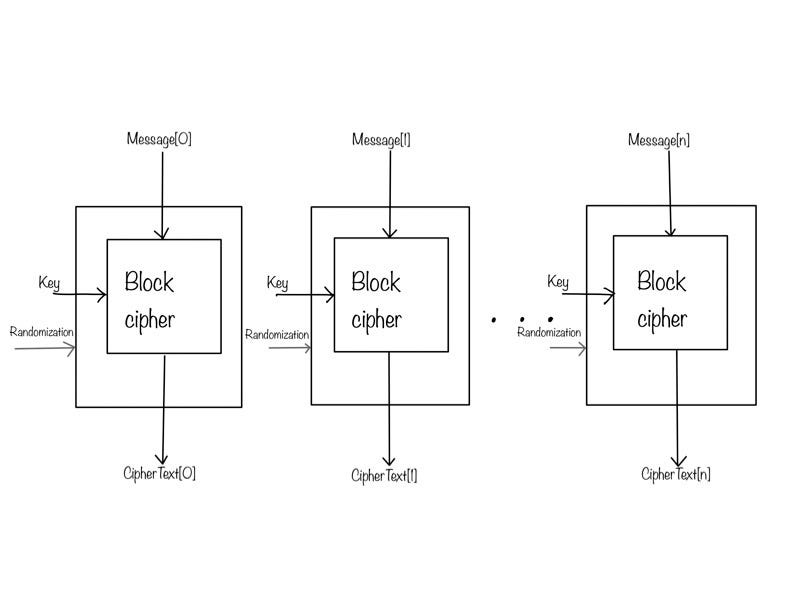
The scope of this article is limited to symmetric key block cipher cryptography. A key, which is known both to the sender and the receiver is used as an input to a block cipher. A block cipher can be thought of as a function that takes message block and key as input and returns a (pseudo-)random string of 0s and 1s as output. (“Pseudo-” random, because during the decryption process this string with the key should return the message block back). The message that needs to be transferred securely is broken down into blocks of specific size known as the block size. The last block is padded to fit the block size. Each message block is optionally-preprocessed using “some randomization”. The processed message block is the other input to the block cipher. The output of the block cipher is a part of the cipher text. A mode is defined that dictates how multiple block ciphers combine to provide the complete cipher text for the long message.
Example: AES-256-CBC using random IV
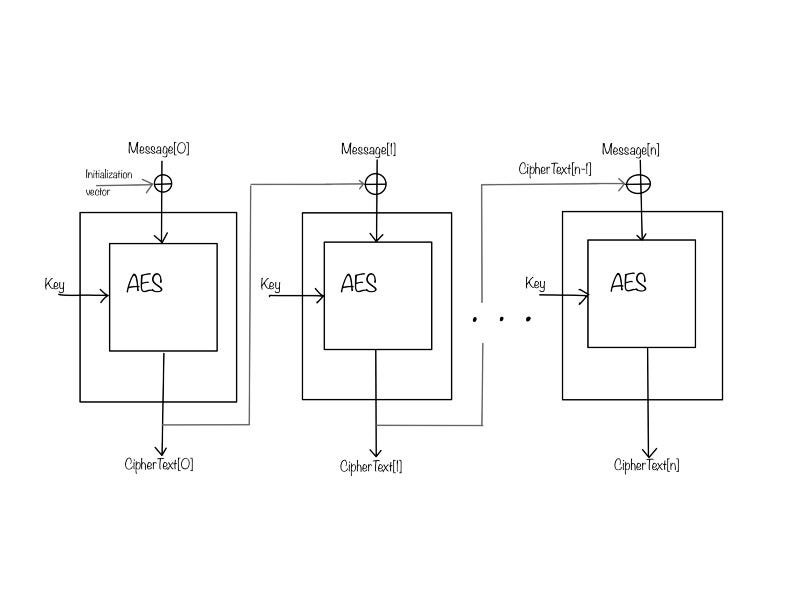
The above image shows the block diagram of AES CBC using a random IV. Here,
AES is the encryption algorithm used by the block cipher.
256 is the key size. In other words, the length of the key is 256 bits.
CBC stands for Cipher Block Chaining mode. It is a mode wherein the previous cipher text block is used as randomization vector for the following block.
Random IV stands for random Initialization Vector. The initialization vector is chosen in random by the sender. This randomly chosen IV is used for preprocessing with the first message block.
The block size for AES is 128 bits. Each message block and the Initialization Vector is 128 bits long.
It is easy said than done!
Now that we understand different building blocks of a cryptographic system and certain terminologies, let us now look into what can go wrong in such systems.
The block cipher
The concepts of Pseudo Random Function (PRF) and Pseudo Random Permutation (PRP) are key to understanding security of block ciphers. https://crypto.stanford.edu/~dabo/cs255/lectures/PRP-PRF.pdf#page=13
A block cipher (also known as PRP) is considered secure if it is indistinguishable from a PRF. The experiment focused on distinguishing the output as an output of a block cipher or that of a random function is known by the term Secure PRF test.
https://crypto.stanford.edu/~dabo/cs255/lectures/PRP-PRF.pdf#page=16
DES, 3DES and AES algorithms are considered to be PRF secure (As of October 30, 2022). However, DES is not used in practice due to its small key size.
The pesudo random generators
Pseudo random generators (PRGs) are functions that output series of 0s and 1s that can be reproducible, but at the same time random enough to disallow an adversary to reproduce it. Similar to block ciphers PRG functions accept a seed and a key to generate a streaming bit string. In fact, secure PRF block ciphers are used to generate random bit strings.
But, what happens if an adversary is able to guess the bit string generated by PRGs? Recall the use of “random” IV in certain modes of encryption. If the random IV is guessable then the fact of considering such encryption mode to be more secure than a mode that uses predefined IV is pointless.
The mode
Similar to Secure PRF test for block ciphers and PRGs, modes are tested for Indistinguishably under Chosen Plain text Attack (IND-CPA) and Indistinguishably under Chosen Cipher text Attack (IND-CCA). This experiment focuses on identifying which of the two input message got encrypted based on the output cipher text returned by an “oracle” ( = E(K,.)) that encrypts one of the two input messages. Intuitively, it means that the experiment ensures that the cipher text does not leak any information regarding the input message(s).
Consider Electronic Code Book (ECB) mode. In this mode of operation, equal messages output the same cipher text. It implies that an adversary collecting a considerable amount of plain text-cipher text pairs can evaluate plain text for future cipher texts. The following slide shows the weakness of ECB mode. https://crypto.stanford.edu/~dabo/cs255/lectures/PRP-PRF.pdf#page=24. Here is a working example guide for breaking AES ECB mode: https://cryptopals.com/sets/2/challenges/12
With evolving security research new schemes are designed and broken, new provable security notions are developed continuously. However, for adoption by industry CBC mode, its variants or better are used. Even though there exists vulnerabilities and weakness in these schemes the exploitation of such systems are handled by the defense in depth, such as by the Intrusion Detection Systems and similar.
The keys
Study of symmetric cryptography assumes that the sender and the receiver already have a shared secret. The shared secret is the key component of the symmetric cryptographic system. Compromise of the key implies compromise of the whole symmetric key cryptographic system.
The challenges that industry faces in terms of storing, using and exchanging keys securely is handled by asymmetric key cryptography and Key Management Systems domains.
Concluding thoughts
In summary, the challenges faced by industry in using symmetric key cryptographic systems are:
Use of a secure proven block cipher, pseudo random generators and encryption/decryption modes.
Handling and managing keys and other parameters (such as random IV) used in symmetric key encryption and decryption.
The field of security is ever changing. It is demanding for organizations to keep up with the latest weaknesses and attacks on cryptographic system. Similar to any vulnerabilities and exploitation, the organization would first respond to it by installing detection rules in its monitoring and detection systems, develop (or) identify a patch to resolve the vulnerability, and develop and deploy the solution across all the subsystem of the organization. It takes days to months to control a vulnerability to its stable state depending on its severity and priority. However, the focus of the organization is to keep the business running while ensuring trust with its customers.
